FIPS 140-2 is the de-facto standard to certify cryptography implemented in ICT products
What is FIPS 140-2?
The Federal Information Processing Standard (FIPS) 140-2 is a U.S. government security standard that specifies the security requirements used to validate cryptographic modules, which must be met in order for products to be validated under the Cryptographic Module Validation Program (CMVP).
For vendors, a successful FIPS 140-2 validation can be essential to selling their products in US and international markets. FIPS 140-2 has also proliferated into other verticals, like healthcare (HIPAA) and the financial industry. Intertek’s experienced Cryptographic Module Validation Program (CMVP) accredited laboratories can help you understand and navigate the process to ensure a successful validation.
FIPS 140-3 is the latest update for validating the effectiveness of cryptographic modules. FIPS 140-3 supersede FIPS 140-2 and is the only submissions being accepted by the CMVP. The standard provides four levels of security intended to cover a range of applications and environments.
Intertek FIPS 140-2 Solutions
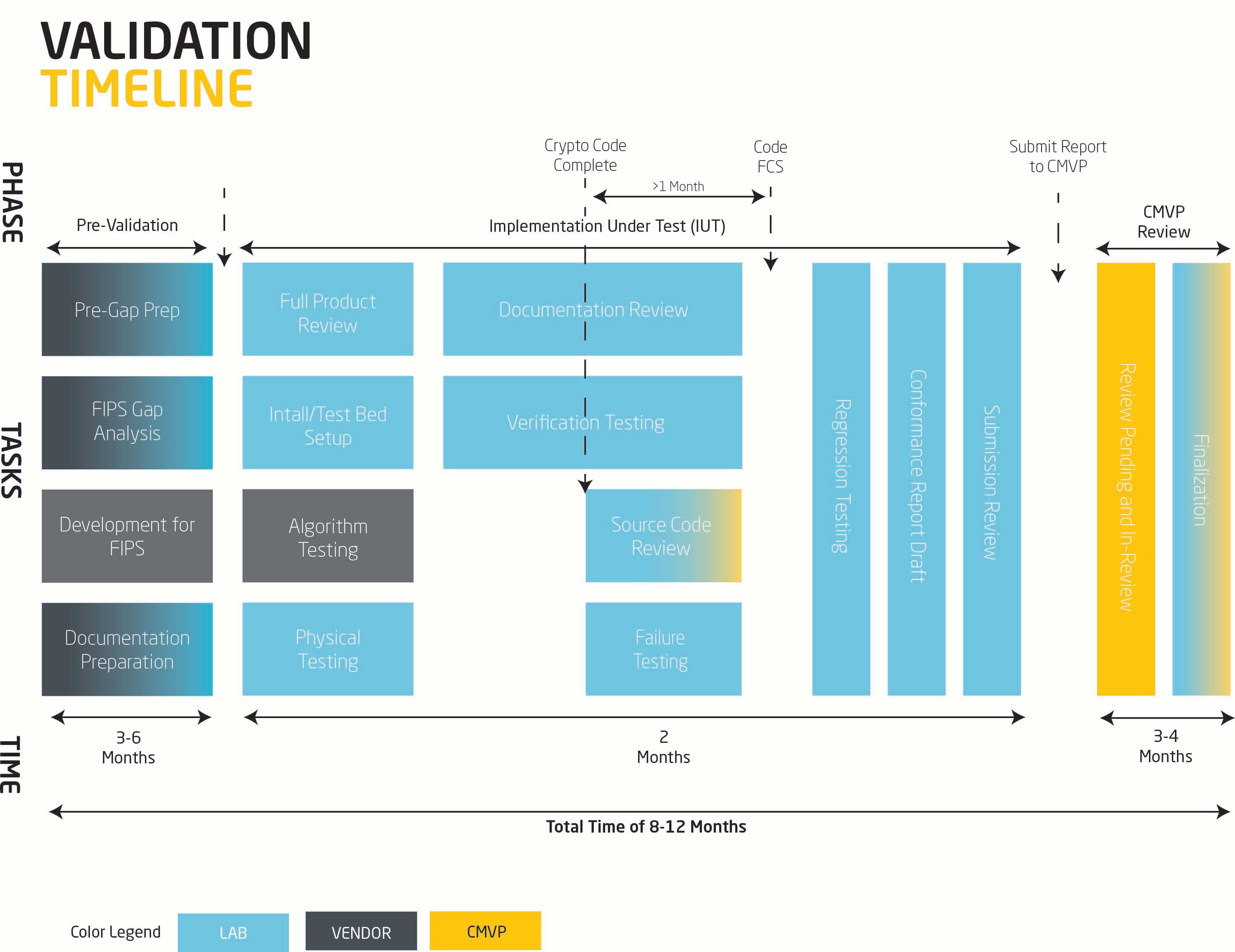
We seek to engage early on and adopt risk mitigating processes whereby non-compliance is identified early on, fixes are discussed and planned, testing methodology is defined in advance to allow your teams to plan accordingly and schedule is tracked religiously to ensure our progress is in step with your development and test plans.
We have leveraged our considerable experience in FIPS 140 validation to develop custom tools and processes to offer a best-of-breed certification experience to our clients.
FIPS 140-3 Validation
For vendors, a successful FIPS 140-3 validation can be essential to selling their products in US and international markets:
- In the U.S., the DoD and NIAP NSTISSP No. 11 require FIPS 140 validation for cryptographic modules used by federal government agencies to store, transmit or protect sensitive, but unclassified information (see section 3.2 of the FIPS 140-3 FAQ for details).
- In Canada, the CSEC recommends federal agencies use FIPS 140 validated cryptographic modules to secure data designated as Protected A or Protected B.
- In the U.K., the Communications-Electronics Security Group (CESG) recommends the use of FIPS 140 validated cryptographic modules.
FIPS 140 Algorithm Testing
Algorithm testing is an important step for the FIPS module validation process. While it is the most objective part of the validation process, it does not require specialized tools or skills to execute.
FIPS 140 Service Offerings:

Knowledge Center
- Cybersecurity Awareness Training Fact Sheet
- Common Criteria Certification Process Fact Sheet
- FIPS 140-3 Process and Service Offerings Fact Sheet
- Cyber Security Risk in a Mass Remote Working Environment Webinar
- Intertek Cyber Assured Fact Sheet
- Consumer Product Focused Cyber Security Test and Certification Program
- PCI PIN Transaction Security (PTS) Cyber Security Fact Sheet
- Cyber Security Assurance Overview
- ANSI/UL 2900 Cyber Security Assessments Fact Sheet
Upcoming Events
Cybersecurity Assurance Overview
Intertek provides tailor-made security solutions designed and executed based upon risk factors commonly associated with your specific product and industry.